DMARC (Domain-based Message Authentication, Reporting & Conformance) protects your email domain from unauthorized use by acting as an email security protocol. It ensures that only authorized senders can send emails from your domain, preventing phishing and email spoofing attacks. Implementing DMARC records can greatly improve your email security, protect your brand reputation, and reduce the risk of fraud.
This blog will explain how it works, and why it’s important for your business. We will also guide you through the steps to implement DMARC records correctly, ensuring that your email system is secure and recipients trust your messages. This step-by-step guide will help you get started with DMARC and improve your email protection, whether you’re new to email security or looking to enhance your setup.
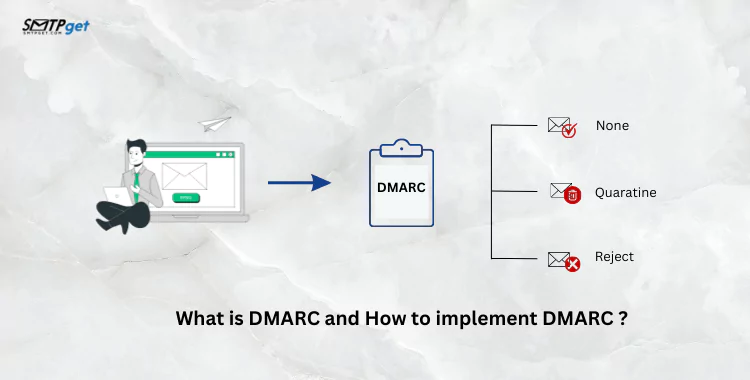
What is DMARC?
DMARC (Domain-based Message Authentication, Reporting & Conformance) is an email authentication protocol created to protect email senders and recipients from phishing and spam attacks. It helps ensure that emails sent from a domain are legitimate and not forged by malicious actors.
DMARC works together with two other email authentication methods: SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail). SPF verifies if an email is coming from an authorized SMTP server, while DKIM checks the integrity of the email’s content. DMARC combines both of these and allows domain owners to set policies for how Bulk email servers should handle messages that fail authentication checks.
It helps improve email deliverability by reducing the chances of legitimate emails being marked as spam. Additionally, it provides reporting tools that give domain owners insights into their email traffic and potential security threats.
Why is DMARC Important?
It helps safeguard your domain from being exploited in phishing and email spoofing attacks. Here’s why DMARC is important:
Protects Your Brand Reputation
Phishing and spoofing attacks can damage your brand’s reputation. Hackers can impersonate your company by sending fraudulent emails and tricking your customers. By using Records, you ensure that only legitimate emails from your domain are delivered, helping maintain trust in your brand.
Prevents Phishing Attacks
Phishing is when attackers send fake emails to steal sensitive information like passwords or credit card numbers. DMARC Records helps detect these fraudulent emails and stops them from reaching inboxes, reducing the risk of phishing attacks targeting your customers.
Blocks Email Spoofing
Email spoofing occurs when attackers forge the sender’s address to make an email appear as if it’s from a trusted source. With DMARC in place, unauthorized senders cannot use your domain to send fake emails, protecting your customers and business from these scams.
Improves Email Deliverability
It helps legitimate emails pass through spam filters and reach your recipients’ inboxes. By using DMARC, you show email providers like Gmail and Yahoo that your domain is secure, which improves the chances of your emails being successfully delivered.
Provides Detailed Reports
This generates reports that give insights into who is sending emails on behalf of your domain. These reports help you monitor unauthorized use and take action if necessary to protect your email sender reputation.
Reduces Fraudulent Activities
By preventing phishing and spoofing, it reduces the chances of fraudsters using your domain for scams, keeping both your business and your customers safe.
How does DMARC work?
Domain-based Message Authentication, Reporting & Conformance is a protocol designed to protect both email senders and recipients from phishing, spoofing, and other types of email fraud. Here’s how DMARC works:
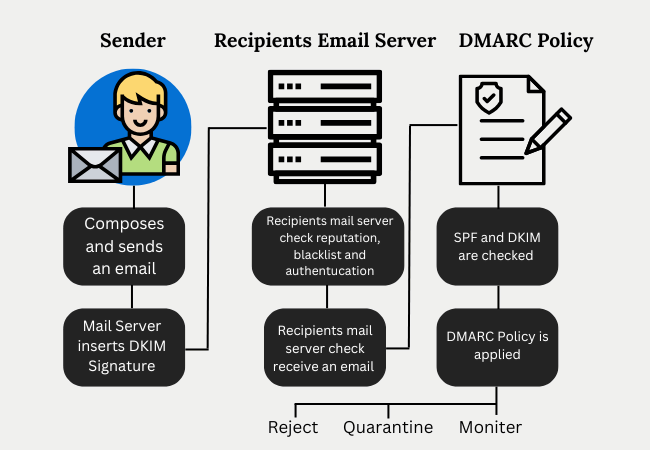
Email Authentication:
- DMARC builds on two authentication methods, SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail).
- SPF checks if the email comes from an authorized IP address for that domain.
- DKIM verifies if the email content has been altered in transit by checking for a valid digital signature.
DMARC Policy:
Once SPF and DKIM are in place, it allows domain owners to set a policy for how their emails should be treated. The policy can be configured to one of three levels:
- None: No action is taken; this is used for monitoring.
- Quarantine: Emails failing authentication are marked as suspicious and may go to the spam folder.
- Reject: Emails failing authentication are completely blocked.
Alignment:
For DMARC to pass, the domain in the “From” header must match the domain used in SPF and DKIM checks. This ensures that the sender’s domain is properly aligned with the email’s authentication methods.
Reporting:
DMARC provides a reporting feature that helps domain owners understand how their domain is being used. These reports give details about emails passing or failing SPF/DKIM checks, helping identify potential security threats.
Protection Against Spoofing:
With DMARC, organizations can prevent unauthorized users from sending fraudulent emails using their domain. This reduces the chances of phishing attacks that trick recipients into revealing sensitive information.
Improved Email Deliverability:
DMARC increases email trust, improving deliverability rates, meaning emails are more likely to land in the inbox instead of the spam folder.
How to Implement DMARC: Step-by-Step Guide
Here’s a simple, step-by-step guide to help you implement better email security:
Understand Basics
It helps prevent unauthorized people from sending emails that appear to come from your domain. It works alongside two other email security protocols: SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail).
Set Up SPF and DKIM First
- Before setting up DMARC, ensure you have SPF and DKIM configured for your domain.
- SPF verifies that the sender is authorized to send emails from your domain.
- DKIM adds a digital signature to your emails to confirm they are genuine.
Create a DMARC Record
- To implement, you need to create a DMARC record in your DNS (Domain Name System).
- The DMARC record is a TXT entry, usually in the format: v=DMARC1; p=none; rua=mailto:dmarc-reports@yourdomain.com.
- The “p” value can be set to:
- none: Monitor only, no action on failed emails.
- quarantine: Mark suspicious emails as spam.
- reject: Reject any emails that fail DMARC checks.
Publish Your DMARC Record in DNS
Add the record to your DNS settings for the domain. This step tells email servers how to handle your emails and report back about suspicious activity.
Monitor DMARC Reports
After setting up, you’ll start receiving reports on how your domain is being used for email sending. Use these reports to monitor your domain’s security and identify any potential issues.
Adjust DMARC Policy Over Time
Start with the “none” policy to gather data. Once you are confident in your email security, move to “quarantine” or “reject” to block fraudulent emails.
Common Record Types
When setting up DMARC (Domain-based Message Authentication, Reporting & Conformance), you need to understand the different types of DMARC records. These records tell email servers how to handle emails that fail DMARC checks. Here are the most common record types:
p=none (Monitor Mode)
- This is the most basic DMARC policy.
- It doesn’t block or reject any emails but collects data about messages failing DMARC.
- Use this record when you’re first implementing DMARC and want to monitor your email traffic before making strict changes.
p=quarantine (Quarantine Mode)
- This policy tells receiving email servers to treat emails that fail DMARC checks as suspicious.
- Emails that fail will be marked as spam or placed in the recipient’s junk folder.
- It’s a good option for organizations ready to enforce stricter email security but still want to keep the emails for review.
p=reject (Reject Mode)
- The strictest policy.
- Emails that do not pass DMARC checks are rejected and won’t reach the recipient.
- This policy is ideal for businesses with strong email authentication practices and who want to completely block unauthorized emails from reaching their audience.
sp=none/quarantine/reject (Subdomain Policy)
- This record applies DMARC rules to subdomains of your domain.
- For example, if your main domain uses p=reject, you can set sp=none to apply a more lenient policy to subdomains.
- It gives you control over how subdomains are handled differently from the main domain.
rua=mailto
dmarc@domainame (Aggregate Report URI)
- This part of the DMARC record tells bulk email servers where to send DMARC reports.
- It’s important for gathering feedback and understanding how your emails are being treated across different servers.
- Use this to track the success or failure of your policy.
ruf=mailto
dmarc@domainame (Forensic Report URI)
- This record specifies where detailed reports about failed emails should be sent.
- These reports contain more specific information, such as the message that failed and why.
- Use it to investigate issues with specific emails in real-time.
How to read and interpret DMARC reports for better email security.
This provides valuable information about how your domain’s emails are being handled by receiving email servers. Here’s what you need to know about the report:
1. What Are DMARC Reports?
DMARC reports are feedback messages sent by email receivers (like Gmail or Outlook) to the domain owner. They contain data about how emails from your domain are being treated. These reports show whether the emails are passing or failing checks, helping you spot potential issues with email security.
2. Types of DMARC Reports:
- Aggregate Reports: These provide summary data about your email’s performance. They show the number of emails that passed or failed DMARC checks.
- Forensic Reports: These give more detailed information about specific emails that failed DMARC checks, helping you investigate any suspicious activities.
3. Key Components of DMARC Reports:
- Policy Evaluations: Reports show whether the email passed the SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail) checks. If both checks fail, the email is likely marked as suspicious.
- Disposition: This tells you what action was taken with emails that didn’t pass DMARC. They may be delivered, quarantined, or rejected.
- Authentication-Results: These show how your emails are performing in terms of SPF and DKIM alignment.
4. Why Are DMARC Reports Important?
- Track Domain Usage: Reports show who is sending emails on behalf of your domain, helping you identify unauthorized senders.
- Improve Email Deliverability: By analyzing reports, you can ensure your legitimate emails reach the inbox and aren’t mistakenly marked as spam.
- Spot Security Issues: Reports help identify phishing or spoofing attempts using your domain, so you can take action quickly.
5. What to Do with DMARC Reports:
- Regularly review your reports to ensure your emails are protected.
- Adjust your policy as needed, depending on the results of the reports.
- Investigate any failed emails to prevent fraud and improve your email security.
Troubleshooting common issues faced during DMARC implementation.
Implementation can greatly improve your email security, but it may come with challenges. Here are a few common issues along with their solutions:
1. Incorrect DNS Record Format
- Problem: If your DNS record is not set up correctly, it will not work as expected.
- Solution: Double-check your record format. Ensure it follows the correct syntax. Use online tools to validate the DMARC record and fix any errors in the DNS configuration.
2. SPF and DKIM Failures
- Problem: DMARC relies on SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail) to verify email authenticity. If these are not set up properly, It will fail.
- Solution: Ensure that SPF and DKIM are correctly configured for all email sources. Utilize tools to verify that your SPF and DKIM records are functioning correctly.
3. DMARC Reports Not Received
- Problem: You may not receive DMARC reports, making it hard to monitor email activity.
- Solution: Ensure that the “rua” (aggregate report) and “ruf” (forensic report) tags in your DMARC record are correctly configured with the appropriate email addresses to receive reports.
4. Overly Strict DMARC Policy
- A “p=reject” policy can reject legitimate emails if they fail DMARC checks.
- Solution: Begin with a “p=none” policy to monitor email activity, and gradually switch to stricter policies like “p=quarantine” or “p=reject” once you confirm that all legitimate sources are properly authenticated.
5. Legacy Systems or Third-Party Email Services
- Problem: Some older systems or third-party services may not pass DMARC checks.
- Solution: Identify all email-sending sources, including third-party services, and ensure they are compliant with DMARC, SPF, and DKIM. You may need to work with SMTP relay services to set up proper authentication.
6. No Alignment Between SPF/DKIM and From Header
- Problem: Needs SPF/DKIM to align with the email’s “From” header. If they don’t align, DMARC will fail.
- Solution: Ensure that the “From” domain matches the domain in the SPF or DKIM check. This alignment is crucial for successful implementation.
How SPF and DKIM work together with DMARC for email authentication.
Email authentication relies on three key protocols—SPF, DKIM, and DMARC—to guard against email spoofing and phishing attacks. These protocols work together to ensure your emails are legitimate and trusted. Here’s how they work:
1. SPF (Sender Policy Framework):
- SPF helps verify that the email is coming from an authorized server.
- It checks the sending server’s IP address against a list of allowed servers in the domain’s SPF record.
- If the server is not listed, the email is considered suspicious and may be rejected or marked as spam.
2. DKIM (DomainKeys Identified Mail):
- DKIM adds a digital signature to the email header, which is unique to the sender’s domain.
- The sender creates this signature using a private key, and the recipient can verify it using a public key stored in the domain’s DNS record.
- If the signature matches, it proves that the email has not been tampered with during transit.
3. DMARC (Domain-based Message Authentication, Reporting, & Conformance):
- DMARC ties together SPF and DKIM by giving domain owners the ability to set policies for handling emails that fail authentication.
- It checks if the email aligns with SPF or DKIM and if the domain in the “From” field matches the one authenticated by SPF or DKIM.
- It provides options for handling unauthenticated emails, such as quarantine or rejection, and sends reports to the domain owner about failed authentication attempts.
4. How They Work Together:
- SPF ensures the email comes from an authorized server.
- DKIM verifies that the email hasn’t been altered during transit.
- DMARC ensures that both SPF and DKIM are correctly applied and reports any failures.
- Using all three together provides strong protection against phishing, fraud, and unauthorized domain use.
How to Monitor Your DMARC Implementation
Once you have set up DMARC, monitoring it is crucial to ensure it works correctly and to detect any issues that could affect email deliverability or security. Here’s how you can monitor your implementation:
1. Check Reports Regularly
- it provides two types of reports: aggregate and forensic reports.
- Aggregate Reports show general statistics on emails sent using your domain, including which emails passed or failed authentication.
- Forensic reports provide in-depth details about specific email failures.
- Regularly review these reports to understand the effectiveness of your DMARC policy.
2. Use Monitoring Tools
- There are several tools available that make monitoring your DMARC implementation easier, like DMARCian, Postmark, or Easy DMARC.
- These tools help you analyze reports, identify issues, and make necessary adjustments to your policy.
3. Set Up Alerts for Failures
- Configure your DMARC monitoring tool to send you alerts if there are any email failures.
- This will help you react quickly to potential issues like unauthorized email senders or misconfigurations.
4. Review Authentication Results
- Look at the DMARC, SPF, and DKIM results in your reports. If emails fail DMARC, check if they also failed SPF or DKIM.
- These failures may indicate problems with your email setup or unauthorized senders trying to misuse your domain.
5. Adjust Your DMARC Policy Gradually
- Start with a “none” policy to collect data, then move to “quarantine” and eventually to “reject” as you become more confident in your email security.
- Monitor the results after each policy change to ensure that legitimate emails don’t get blocked.
6. Check Email Deliverability
- Monitor how recipients are receiving your emails.
- If you notice a drop in email deliverability, check your reports for signs of issues.
7. Review Authentication Changes Regularly
- If you add or remove email services (like third-party senders), make sure their email authentication aligns with your policy.
- Update your SPF and DKIM records accordingly.
Regularly monitoring your implementation ensures your domain stays secure and recipients trust your emails. Regular checks and adjustments will improve your email security over time.