Have you ever wondered how your emails prove they’re really from you? Or why do some emails end up in spam while others land safely in the inbox? It’s not just about luck—it’s about authentication. One important email authentication tool is DKIM (DomainKeys Identified Mail). DKIM helps ensure that the emails you send are verified as coming from your domain, keeping your reputation intact and your messages trusted.

For email providers to prevent a form of spam and other types of email fraud, email authentication is important. A keystone of this defense is DomainKeys Identified Mail (DKIM). With the addition of a digital signature by DKIM, emails can be verified as coming from an official source by the recipient’s email server. If this sounds like another confusing acronym, don’t worry! We’ll walk you through DKIM, how it works, and why it’s essential for secure and successful email communication. Let’s explore more about DKIM Email Authentication and why it is important for SMTP Server Provider.
Our Pricing:
| Pricing | Cheapest Plan | Standard Plan | Professional Plan |
| SMTP Server Services | $110 | $165 | $220 |
| Bulk Email Server | $50 | $145 | $225 |
| Bulk Email Service | $30 | $110 | $220 |
What is DKIM key authentication?
DKIM (DomainKeys Identified Mail) is an important tool in email authentication protocol. It helps verify that an email truly comes from the sender it claims to be from. DKIM works by adding a digital signature to each email, which is then validated by the receiver’s mail server. This signature is linked to your domain and can’t be faked by others, ensuring that no one can pretend to send emails from your domain. DomainKeys Identified Mail, or DKIM, is an important email authentication technique that fights fraud and email spoofing. It functions by encrypting outgoing emails with a digital signature that the recipient’s email server can confirm. The sender domain’s private key is used to build this signature, which is verified by the matching public key that is listed in the domain’s DNS record.
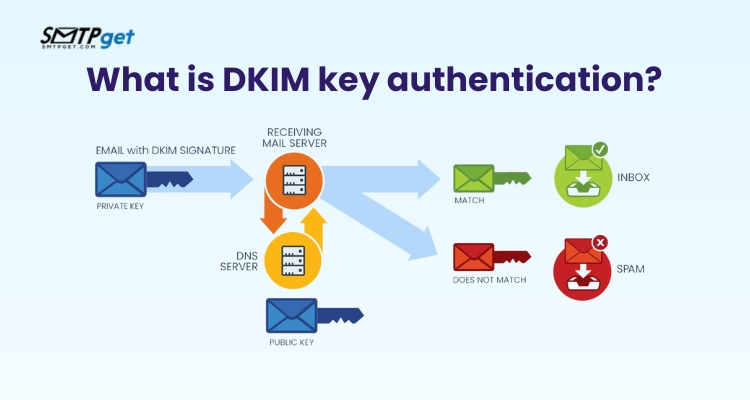
DKIM Email Authentication is important, Whether you’re sending marketing or important transactional emails, using DKIM builds trust with email providers and recipients. Without DKIM, your emails might be flagged as suspicious, increasing the chance they will be marked as spam. DKIM not only protects your brand’s reputation but also improves email deliverability. It’s a simple yet powerful way to ensure your emails are trusted and reach their destination safely.
Why is DKIM authentication important for email security?
DKIM works by digitally signing outgoing emails and adding a unique signature to the email header. When the recipient’s SMTP server for email marketing receives the email it checks the signature against the public key stored in the sender’s DNS record. If the signature is valid it confirms that the email has not been played around with during transit.

The capacity of DKIM Email Authentication to prevent scams, email spoofing, and the distribution of harmful malware makes it crucial. Additionally, it improves the sender’s domain’s credibility and repute. Organizations can lower their exposure to email-based risks, safeguard sensitive data, and guarantee secure communications by integrating Authenticate Email with DKIM. For this reason, DKIM authentication is essential to maintaining the security and integrity of email correspondence.
How does DKIM authentication work to prevent email spoofing?
DKIM (DomainKeys Identified Mail) is an Email Authentication DKIM method that helps verify the authenticity of email messages. It safeguards against email spoofing and phishing attacks, ensuring that emails sent on behalf of a domain are legitimate.
DKIM operates by adding a digital signature to outgoing email messages. Here’s how it works:

Generating a Signature: The sending mail server creates a unique cryptographic signature using the private key associated with the sending domain.
Adding the Signature: The signature is added as a DKIM header in the email message’s metadata.
Receiving Mail Server Verification: The receiving mail server retrieves the public DKIM key from the DNS records of the sending domain.
Verification: The receiving server uses the public key to verify the email’s signature. If the signature is valid, the email is considered authentic.
By enhancing email receivers’ ability to trust the sender, DKIM lowers the possibility that they may accept fake communications. It safeguards against email-based cyber risks and is an essential part of email security.
Benefits of DKIM authentication for email marketing
Email marketing is a powerful tool for businesses to connect with their audience, but it’s essential to ensure the security and authenticity of your emails. DomainKeys Identified Mail (DKIM) is a crucial authentication method that offers several benefits for SMTP service provider email marketing campaigns.

Enhanced Deliverability: SPF DKIM Authentication adds a layer of trust to your emails, reducing the likelihood of them being flagged as spam. This increases the chances of your messages reaching the recipient’s inbox.
Improved Sender Reputation: DKIM authentication helps establish a positive sender reputation, which is vital for long-term email marketing success. A good sender reputation can lead to higher open rates and engagement.
Protection Against Spoofing: DKIM Authenticated emails prevent cybercriminals from impersonating your domain, ensuring that your recipients only receive emails from legitimate sources.
Brand reliability: Authenticity and trustworthiness are essential for building a strong brand image. DKIM-verified emails instill confidence in your recipients, which can lead to better customer relationships.
Regulatory Observation: Some email regulations and industry standards, like GDPR, require email authentication. Email Authentication DKIM helps you meet these requirements and avoid potential legal issues.
Step-by-Step guide to setting up DKIM authentication for custom domain
One essential component of email security is (DomainKeys Identified Mail) DKIM authentication. DKIM helps verify the authenticity of emails by adding a digital signature to outgoing messages. To set up SPF DKIM Authentication, follow these steps:
Generate DKIM keys: Begin by generating a pair of DKIM keys, a private key, and a public key. Most email service providers offer tools to create these keys.
DNS record setup: Publish the public key as a DNS TXT record for your domain. This record will be used by receiving mail servers to verify the email’s authenticity.
Configure email server: Adjust your email server settings to include the private DKIM key when signing outgoing emails.
Test your setup: Send test emails and check the DKIM signature. Various online tools can help you verify the correctness of your configuration.
Monitor and maintain: Regularly monitor your DKIM setup to ensure that it continues to work correctly and update keys when necessary.
How DKIM Impacts Email Deliverability
Using cryptographic keys, DKIM adds a digital signature to the email header. The public key provided in the sender’s DNS records can be used by the recipient’s email server to validate the signature of an email when it is received. This procedure assists in preventing spoofing and scams in addition to verifying the legitimacy of the email.
Email deliverability can benefit from a genuine DKIM signature in a number of ways. Authenticated mails are more trusted by email providers, which first improves the sender’s reputation. In turn, this reduces the possibility that your emails will be flagged as spam. Second, it increases the likelihood that the receiver will see your emails in their inbox as opposed to their spam bin, which raises the open and click-through rates.
Importance of DKIM Email Authentication
However because spam and scam emails are so common, it’s imperative to make sure that emails are authentic and genuine. An essential tool in this effort is DomainKeys Identified Mail (DKIM), which provides a reliable way to confirm the legitimacy of email senders.
With DKIM, emails are sent with a digital signature attached, which enables the recipient’s server to confirm the message’s origin. The email was not changed during transit thanks to the use of cryptographic keys linked to the sender’s domain in the generation of this signature. Organizations can successfully combat phishing efforts, email spoofing, and the spread of harmful material by utilizing DKIM.

The importance of DKIM email authentication cannot be overstated. Because recipients may be certain that the message they get is authentic, it promotes trust in email conversations. Additionally, it increases email deliverability rates because emails with valid DKIM signatures are more likely to be delivered to the inbox by email providers than to be tagged as spam.
DKIM email authentication is an essential tool for safeguarding email communication, protecting recipients from malicious actors, and enhancing the credibility of senders. Implementing DKIM is a prudent step for both individuals and organizations to ensure the security and authenticity of their email correspondence.
Pros & Cons of DKIM Email Authentication
DKIM (DomainKeys Identified Mail) is an email authentication system that checks the authenticity of an email message’s sender. Although DKIM is essential for improving email security, it has drawbacks as well.

Pros:
Improved Deliverability: DKIM Authentication helps emails pass through spam filters, ensuring that legitimate messages reach recipients’ inboxes.
Authentication: It verifies that the email’s sender is authorized to send messages on behalf of the domain, reducing the risk of phishing and spoofing.
Reliability: DKIM builds trust by confirming the integrity of an email, which is crucial for businesses and organizations.
Message Integrity: It detects any alterations made to the email during transit, assuring the recipient that the content is unchanged.
Cons:
Complex Implementation: Setting up DKIM can be challenging for users with limited technical expertise, potentially leading to configuration errors.
Maintenance: Regular key rotation and maintenance are necessary, which can be time-consuming.
Compatibility Issues: Some email servers and clients may not fully support DKIM, potentially causing issues with message delivery.
False Positives: Overly strict DKIM policies can result in legitimate emails being marked as spam.
Although DKIM offers substantial benefits in terms of email security and reputation, it must be carefully implemented and maintained to prevent any negative effects. Combined with other email authentication techniques like SPF and DMARC, it can offer a strong security against threats via email.
Conclusion
Strong technology called DKIM (DomainKeys Identified Mail) allows recipients of emails to confirm the validity of the sender’s domain. To sum up, DKIM protects the integrity of email content and lowers the risk of email fraud. It improves email security, increases recipient confidence, and eventually makes the email ecosystem safer and more dependable. To defend against email-based attacks, businesses, and email providers should give priority to installing DKIM as part of their email authentication strategy.